Hackers don’t care if it is your birthday, Christmas or New Years Eve.
That’s what the UK foreign currency firm Travelex learned on the last day of 2019 and what we all should be aware of. Travelex currency exchange company’s stores, airport counters and exchange services were forced to go offline after it was discovered a ransomware attack on December 31.
This attack not only affected Travelex, but also many banks such as HSBC, Barclays, Sainsbury’s Bank, Royal Bank of Scotland and many others, which have been using its services and were therefore unable to fulfill foreign currency orders for their customers as a result of the accident. The malware is thought to have caused encryptions of the company’s files and of some customers’ datas, but the firm states that no data has been stolen through the attack.
Who was behind this attack?
It is the Sodinokibi ransomware strain, also known as REvil, a ransomware-as-a-service (RaaS) model, discovered in April 2019. Its infection methods include exploiting known security vulnerabilities and phishing campaigns. It targets Windows systems and encrypts important files asking for a ransom to decrypt them.
Sodinokibi ransomware has been behind different high-profile cyber-offenses in the past year. It was responsible for the attack on 22 Texas municipalities, many dental practices across the United States, a New York Airport and the US data center provider Cyrus One to name a few and it shows no signs of slowing down.
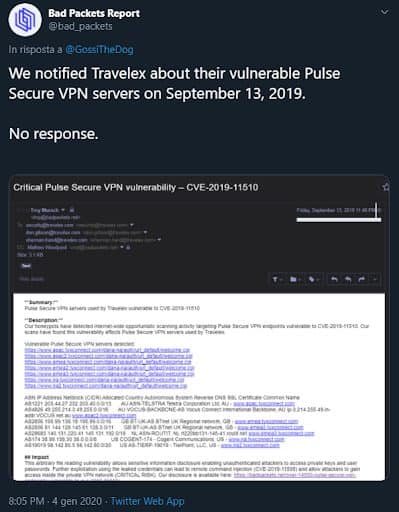
According to the security company Bad Packets, the attack was successful because Travelex waited months to patch critical vulnerabilities in its Pulse Secure VPN servers. In August Bad Packets found 14.500 endpoints that were directly exploitable, results that included governments and some important companies such as Travelex, which had seven unsecured servers due to this wait in patching. Bad Packets also commented that Travelex was notified about the issue (Travelex declined comments on the matter).
How should you protect yourself from Sodinokibi?
The least you can do are these 3 following precautions:
- Be sure to always have all your software and extension to the latest update
- Watch out for harmful phishing emails and don’t open attachments that are unsolicited and might not be trusted
- Backup your files remotely, being sure to use strong passwords and two-factor authentication.
If you want to know more about our services, do not hesitate to contact us!
Source: https://badpackets.net/over-14500-pulse-secure-vpn-endpoints-vulnerable-to-cve-2019-11510
Author: Mattia Pietromartire