Today we continue with the second part of the guide on OWASP, in which we will follow the point where we left it in the first part of the guide.
OWASP Testing Guide
The OWASP Testing Framework is hardly the only one out there, (check PTES, PCI DSS, NIST, ISSAF or OSSTMM), yet it is one worth knowing for any Pentester, especially for those dedicated to Web testing. It is also not the only testing guide OWASP has, since they are also working on testing guides like the ones for Mobile and IoT:
- https://www.owasp.org/index.php/IoT_Testing_Guides
- https://www.owasp.org/index.php/OWASP_Mobile_Security_Testing_Guide
You can find the syllabus here, with links to each section:
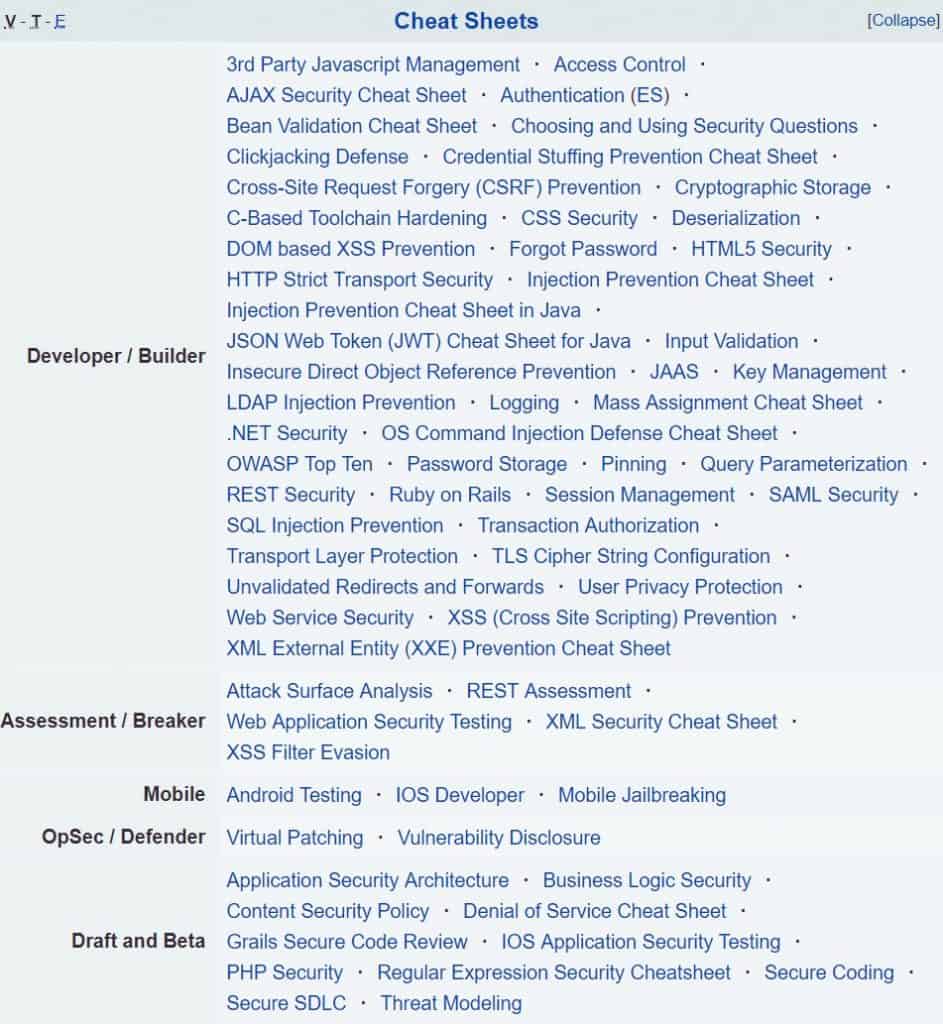
Cheat sheets
No matter what technology you are using, they have a cheat sheet that will help you avoid making common security mistakes. They also have them for security assessments, defenders…
Other projects
Besides those indicated above, there are hundreds of other projects taking place inside the OWASP infrastructure. Here are some interesting ones:
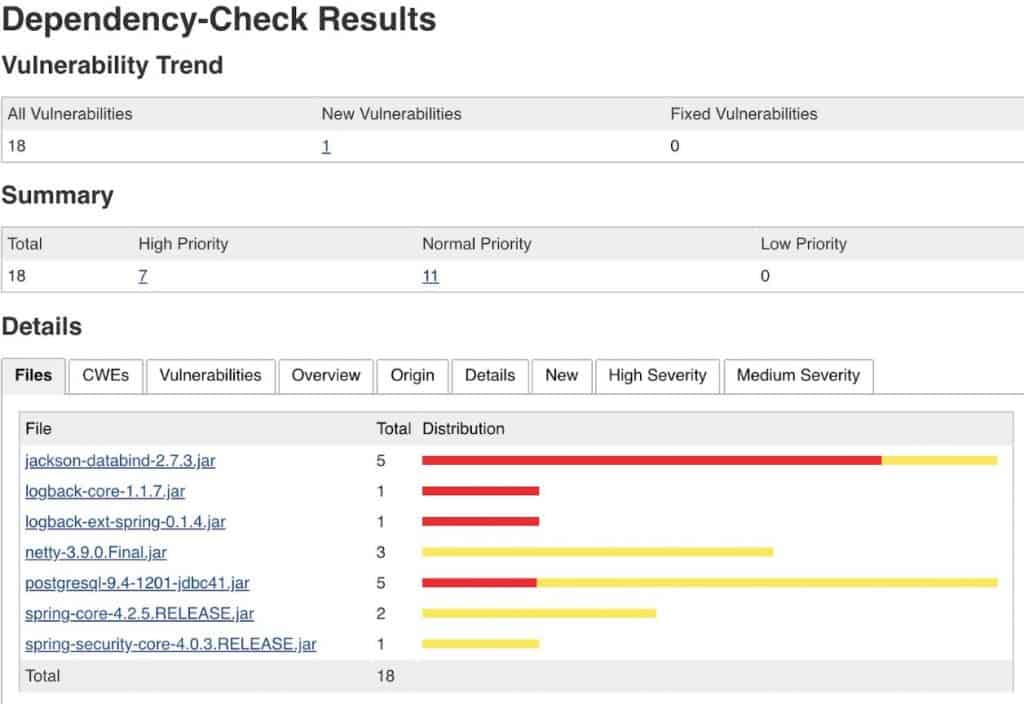
OWASP Dependency Check
This is a handy utility that identifies project dependencies and checks if there are any known, publicly disclosed, vulnerabilities.
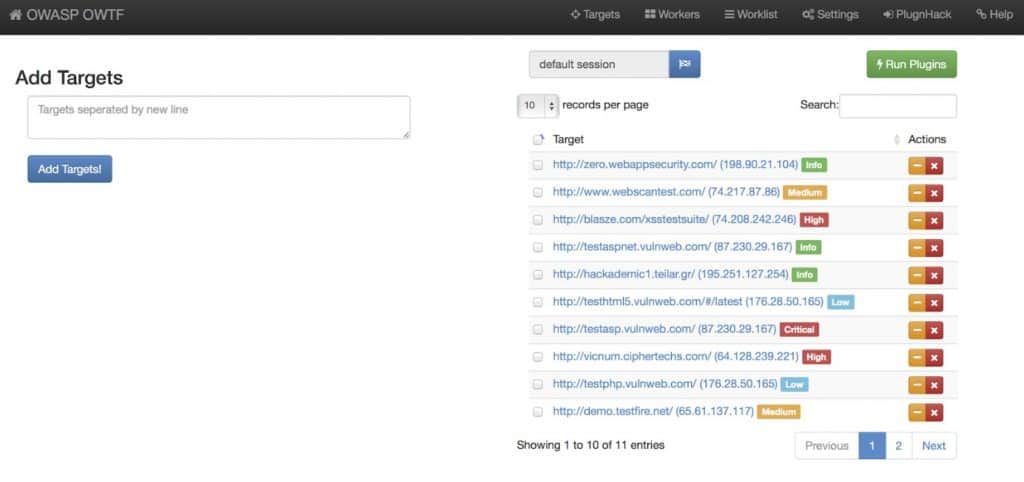
OWASP Offensive Pentesting Frameworks
This project is perfectly aligned with the OWASP Pentesting Guide (above) and can help saving time during pentests by automating repetitive tasks.
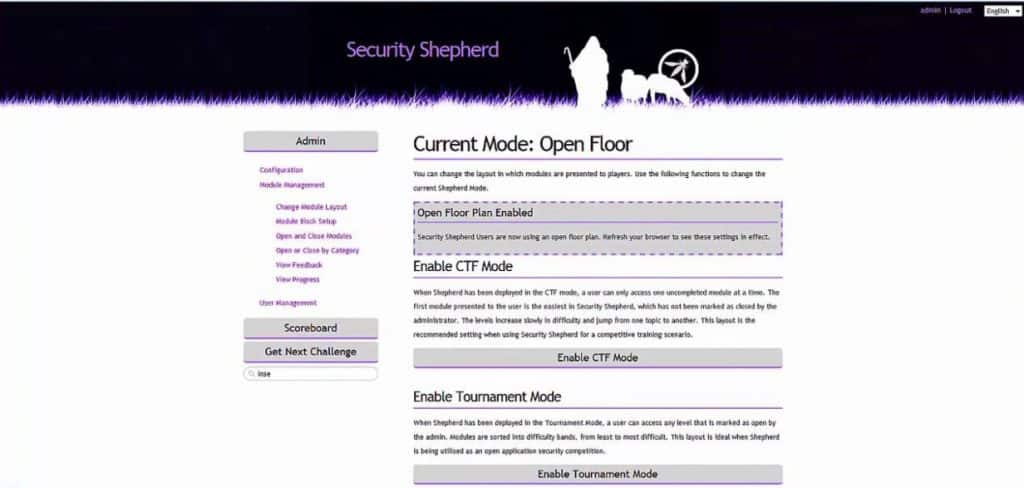
OWASP Security Shepherd
Fun to play with, the OWASP Security Shepherd is a web and mobile application security training platform, where you hone your skills as a security pentester.
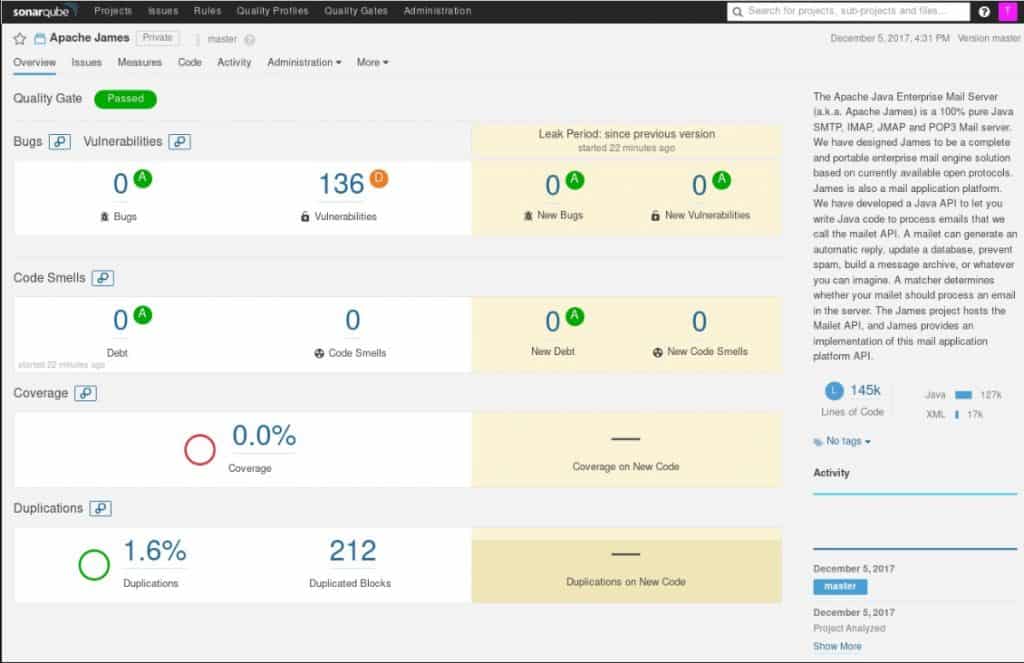
OWASP SonarQube Project
A set of open source solutions designed to analyze application source code. It is made out of 4 components:
- One SonarQube Server
- One SonarQube Database
- Multiple SonarQube Plugins installed on the server, possibly including language, SCM, integration, authentication, and governance plugins
- One or more SonarScanners running on your Build / Continuous Integration Servers to analyze projects
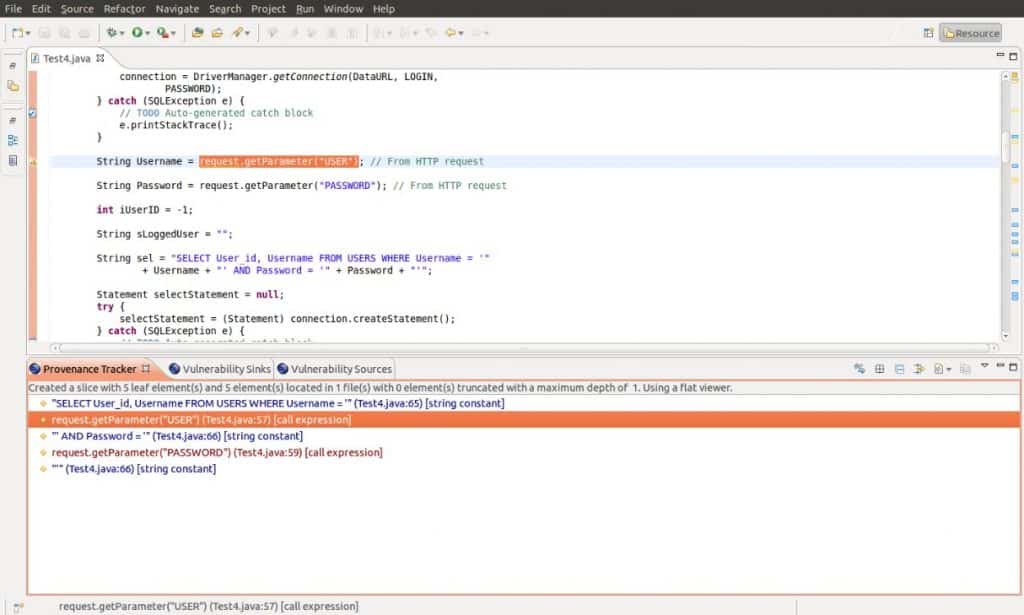
OWASP LAPSE Project
The Security Scanner for Java EE Applications is focused on vulnerability detection in these applications through static code analysis, due to the importance and difficulty of this type of analysis to detect security flaws in them. The vulnerabilities detected by LAPSE+ are related to the injection of untrusted data to manipulate the behavior of the application. This type of vulnerabilities is the most common in web applications.
__
Author: Alejandro Ramírez