iPhone is considered the most unhackable smartphone, especially thanks to the fact that it is a closed OS so nobody can see what’s going on under the hood and spot a vulnerability (better said it’s difficult to). But recently, a group of Google’s Project X researchers have found that you can be infected with a malware by simply visiting a website.
The announcement was made on the 29th of August and the attack worked like this:
- Attackers compromise a bunch of website
- A chain of 15 different vulnerabilities was used for crafting 5 different exploits with at least one 0-day (vulnerability unknown at the time) that can exploit iOS version from 10 to 12.
- When an iOS user visits the hacked website it’ll be infected.
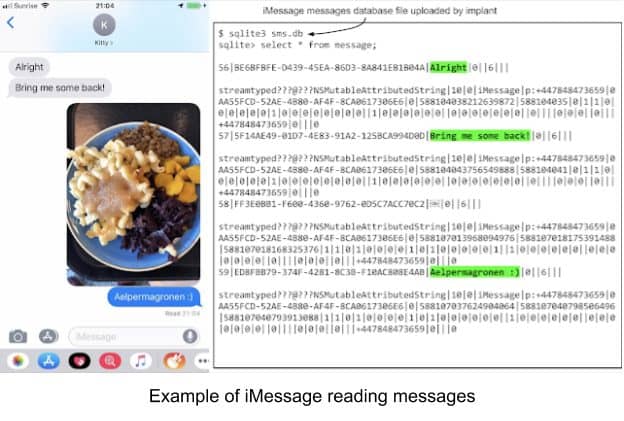
- Attacker can steal sensitive information, geocall, access to keychain, where all the password are stored, and even read the end-to-end encrypted chat from iMessage, WhatsApp and Telegram.
But there is good news, the attack doesn’t have persistence so if the user reboots the iDevice the malware will be wiped out.
And if you think that you are immune because you don’t visit any of the compromised websites you are wrong because an attacker can send you an SMS that appears to come from your gas company/bank/friend inviting you to visit a compromised website, maybe hiding the original URL with the help of online short link generator.
It is not clear who is behind these attacks but we all know about the cost of a single iOS exploit (up to 1 million dollar) and here we have at least one 0-day. We are talking about a team of hackers with a lot of financial resources and capabilities that has been operating for at least two years. All the proofs point to some state-sponsored campaign. Apple has confirmed that the iOS exploits targeted Uighurs, a minority that lives in the north of China, and claimed that all the vulnerability was already fixed when the Project Zero article came out.
If you are concerned about your mobile security or you want to know more about pentesting services, do not hesitate to contact us!
Author: Mattia Pietromartire
Sources:
Google’s Project Zero article: https://googleprojectzero.blogspot.com/2019/08/a-very-deep-dive-into-ios-exploit.html
The Apple statement: https://www.apple.com/newsroom/2019/09/a-message-about-ios-security/